Authentication settings
In authentication page you can set up secondary authentication systems such as OAuth/LDAP/AD for DQM users
General options

Create user on first log in - Users from secondary authentication systems will be created automatically with role 'user' on initial login
Enable OAuth - Enable secondary authentication for OAuth
Enable LDAP/AD - Enable secondary authentication for LDAP/AD
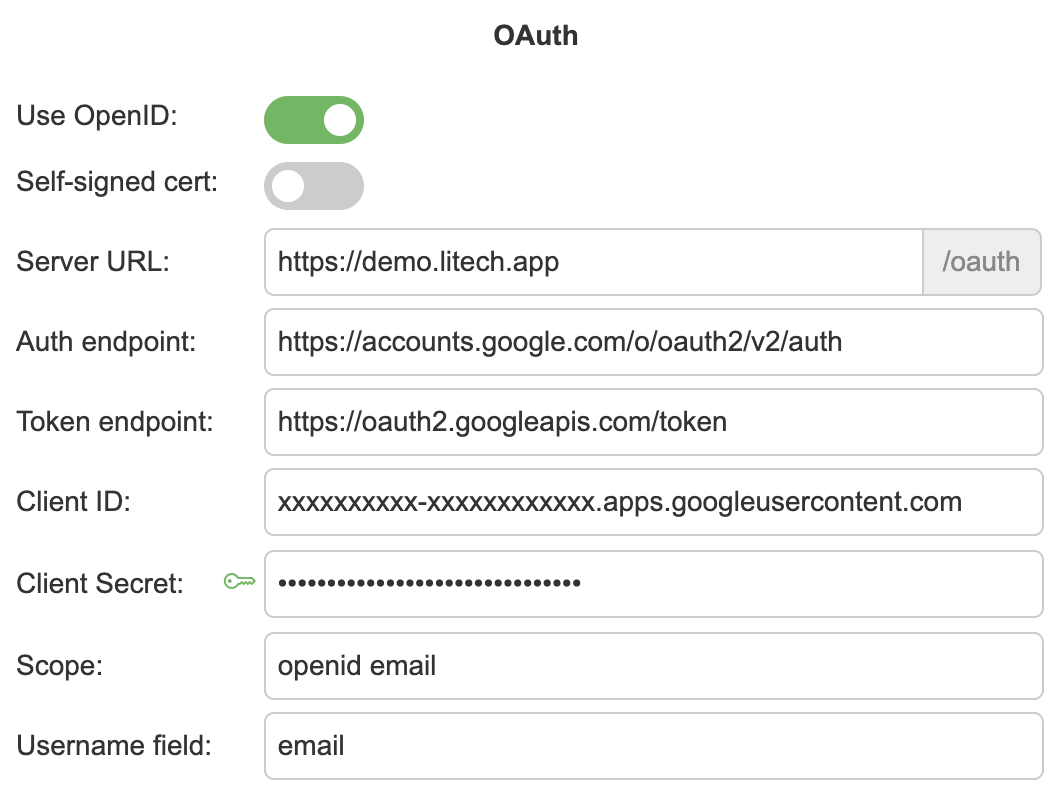
Use OpenID – enable OpenID for OAuth endpoint
Self-signed cert – Force OAuth to validate self-signed certificate from provided certificates
Server URL – URL where current DQM deployment is hosted
Auth endpoint – OAuth server authentication endpoint
Token endpoint – OAuth server token endpoint
Client ID – OAuth client ID
Client Secret – OAuth client secret (Can be entered, when key icon is green)
Scope – OAuth authorization scope
Username field – OAuth username field
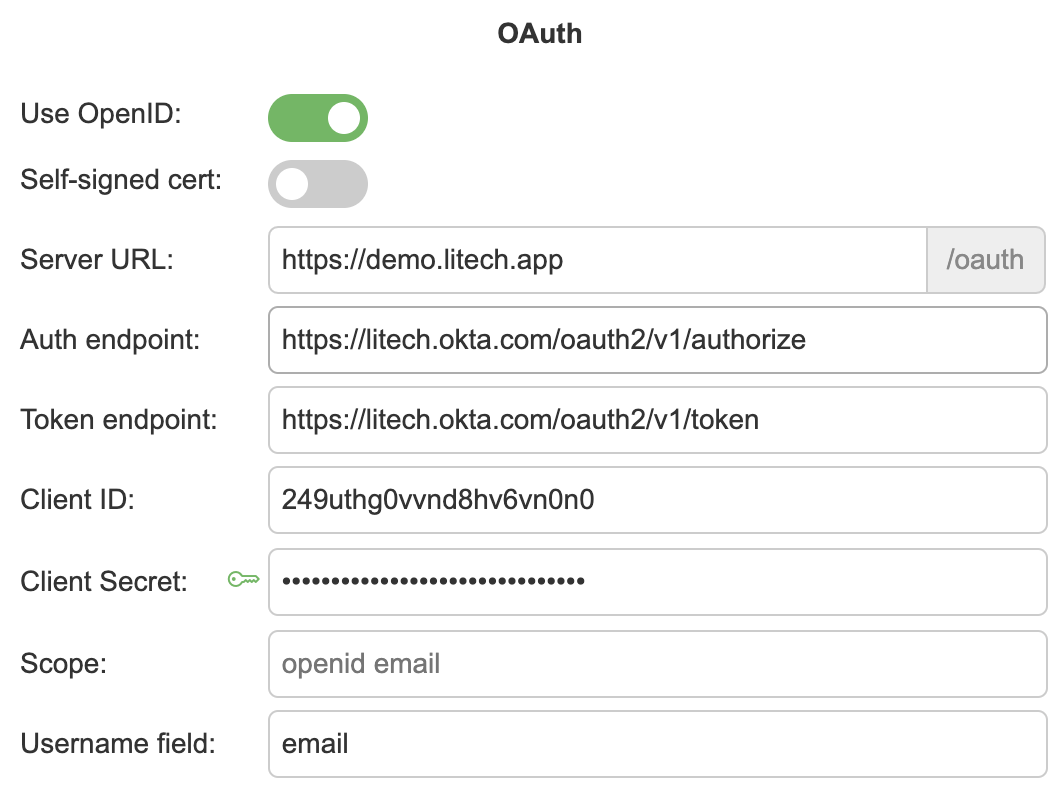
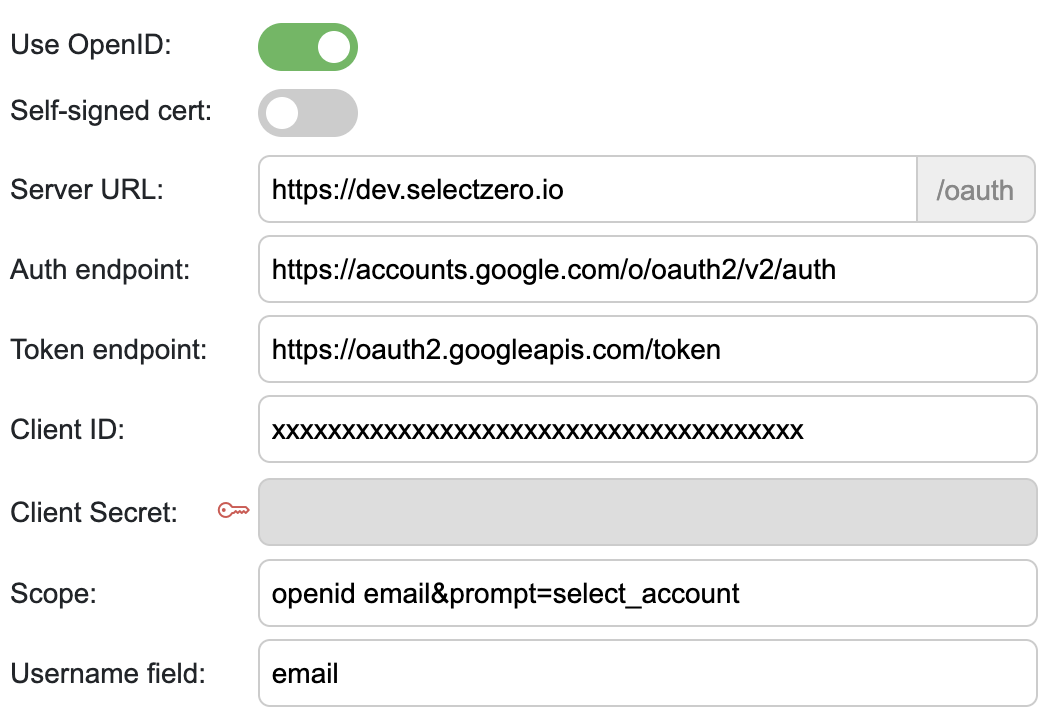
Examples:
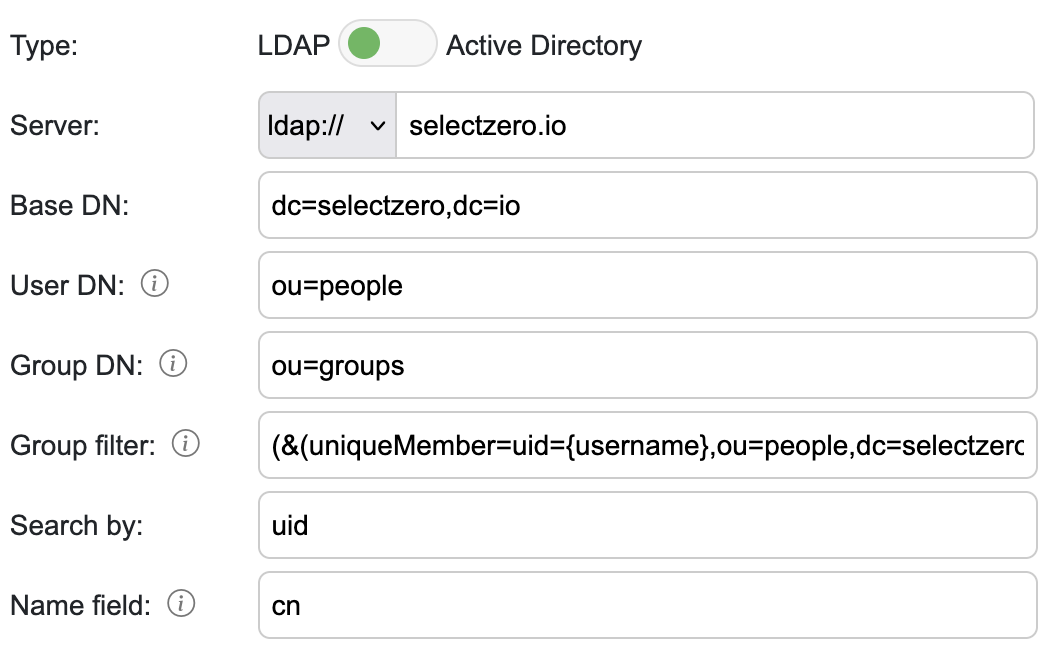
Server – LDAP server, either ldap or ldaps (when using custom port you can include it in the url)
Base DN – LDAP server root distinguished name (If group name has whitespaces then wrap it between quotes e.g. OU=”group name”)
User DN – Optional user DN which will be prepended to base DN for user search
Group DN – Optional group DN which will be prepended to base DN for group search
Group filter – For LDAP we can do additional query to see if user belongs to a certain group. For example:
(&(objectClass=groupOfUniqueNames)(uniqueMember=uid={username},ou=people,dc=selectzero,dc=io)(cn=developers))objectClass - searchable object class 'groupOfUniqueNames'
uniqueMember - LDAP group unique member attribute, where {username} is the placeholder
cn - group where we want to search the member from
Search by – LDAP filter for search user (for example uid)
Name field – If "Create user on first log in" is enabled, we can assign display name from user attribute
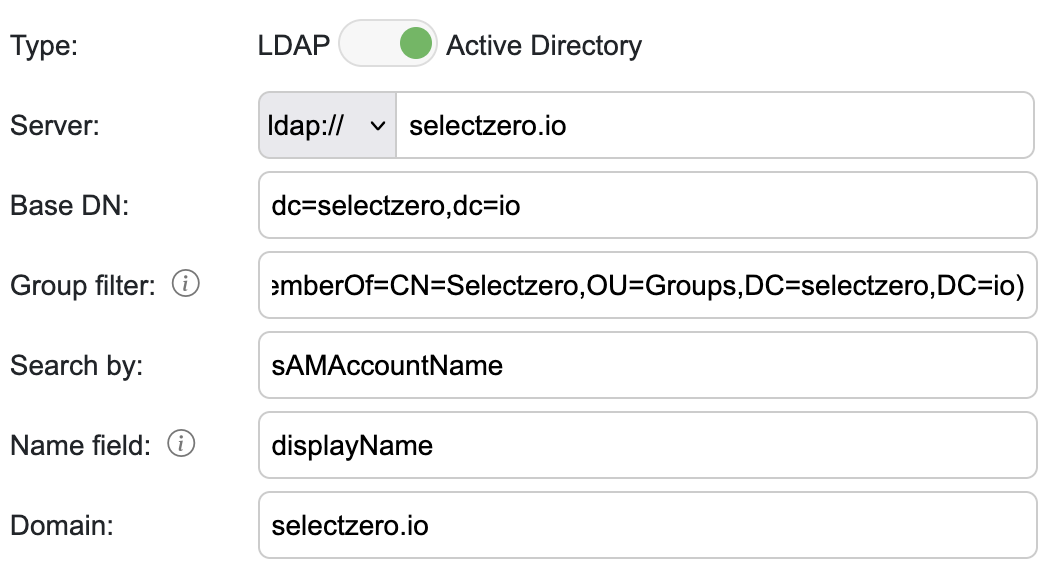
Server – AD server, either ldap or ldaps (when using custom port you can include it in the url)
Base DN – AD server root distinguished name (If group name has whitespaces then wrap it between quotes e.g. OU=”group name”)
Group filter – For AD we can include filter with our AD user query for checking user group. For example:
(memberOf=CN=Developers,OU=Groups,DC=selectzero,DC=io)memberOf - group DN to search for
Search by – AD filter for search user (for example sAMAccountName)
Name field – If "Create user on first log in" is enabled, we can assign display name from user attribute
Domain – AD domain
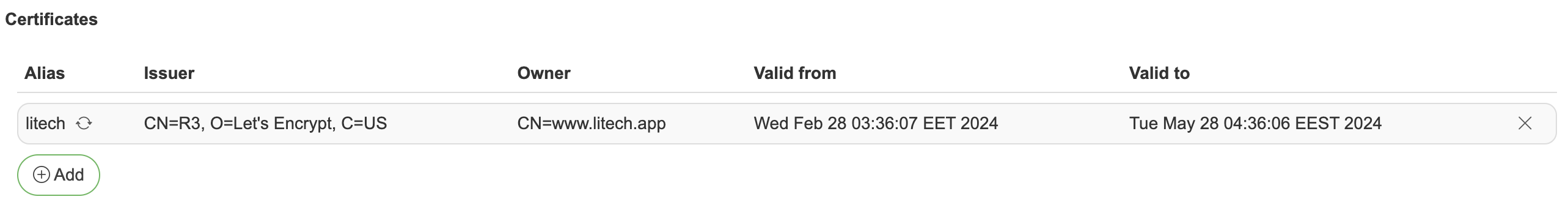
Certificates
In certificates section you can add custom certificates in case any authentications/connections uses TLS/SSL.
Adding a certificate
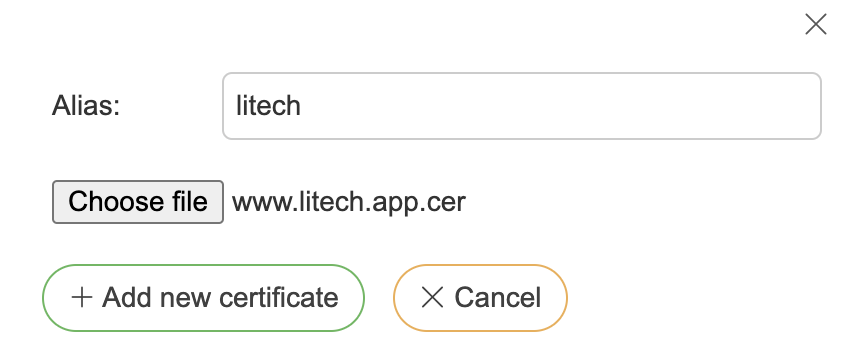
Press “Add” button under certificates section
Choose a certificate file
Give certificate an alias for distinction
Press “Add new certificate”
Adding an https certificate (Enabling HTTPS for DQM)
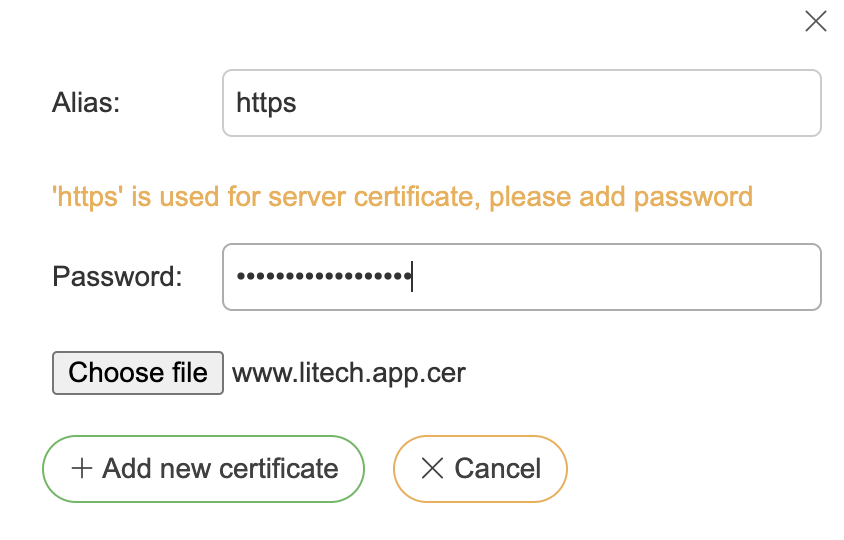
Press “Add” button under certificates section
Choose a certificate file
Give certificate an alias “https” (which is only used for https enabling. Certificate file has to be either .p12 keystore containing RSA private key or .pem file containing RSA private key and certificate chain)
Insert password if certificate is protected by one
Press “Add new certificate”
Tool will shut down automatically
Manually start DQM container/WAR file from server side
Replacing a certificate
Press
 button under certificate row
button under certificate rowChoose new certificate file
Press “Change certificate”
If you replaced “https” certificate, you should reload settings from “Load settings” button on the same page